Latest Technology
for Advanced Threat Protection:

 – Tracking and Applying Threat Databases : Inspecting online databases, evaluating the threats and selecting and applying the necessary rules to prevent threats is a must for a security employee. There are a few challenges; one of them is doing it as soon as possible, so the intruders won’t be able to use known threats against you, and second challenge is to do it 24 hours a day in whole 7 week days, whole year (!), without stopping. It ain’t a human’s job, right? We covered it.
– Tracking and Applying Threat Databases : Inspecting online databases, evaluating the threats and selecting and applying the necessary rules to prevent threats is a must for a security employee. There are a few challenges; one of them is doing it as soon as possible, so the intruders won’t be able to use known threats against you, and second challenge is to do it 24 hours a day in whole 7 week days, whole year (!), without stopping. It ain’t a human’s job, right? We covered it. – Tracking News and Applying Preventions : Inspecting online news and events that are not currently converted into databases, evaluating the threat causes, turning them into an action data and applying the necessary rules to prevent similar threats, is a hard and necessary job, it prevents you from both advanced threats, zero-day attacks and from early rising viruses. Same humanity challenge goes here; doing it as soon as possible, and doing it 24/7 without stopping. We got it covered.
– Tracking News and Applying Preventions : Inspecting online news and events that are not currently converted into databases, evaluating the threat causes, turning them into an action data and applying the necessary rules to prevent similar threats, is a hard and necessary job, it prevents you from both advanced threats, zero-day attacks and from early rising viruses. Same humanity challenge goes here; doing it as soon as possible, and doing it 24/7 without stopping. We got it covered. – Tracking Roaming Files and Inspecting Local Files : Although using different detection systems for file-based attacks by e-mail filters, firewall spam filters, antivirus scanners etc. still, files are complicated threats in a network environment. In order to eliminate file threats, you still have to track roaming files in Internet, classify them as harming / unharming clean files, even detect their true intention (!) because they can be coded for hiding harming intention. It is a team job actually, which we also covered it.
– Tracking Roaming Files and Inspecting Local Files : Although using different detection systems for file-based attacks by e-mail filters, firewall spam filters, antivirus scanners etc. still, files are complicated threats in a network environment. In order to eliminate file threats, you still have to track roaming files in Internet, classify them as harming / unharming clean files, even detect their true intention (!) because they can be coded for hiding harming intention. It is a team job actually, which we also covered it. – Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered.
– Hyperactive Threat Inspection : Determining a recently started attack; gathering it’s details and applying prevention just before it spreads? It is a security pro-work. We got it covered. – Live Traffic Analysis : Inspecting a traffic without violating user privacy is a sensitive issue. Without gathering all the user traffic information and analyzing user trends, which is a violation of privacy ethics, we do analyze connection protocol behaviors and following created unintentional connections towards an Internet address. It doesn’t matter if it is a new site or a cached site, even it isn’t included in any databases, a recently started traffic is analyzed on the fly; without privacy violation, and determined either intentional or unintentional connection. It is a security pro-work. We got it covered.
– Live Traffic Analysis : Inspecting a traffic without violating user privacy is a sensitive issue. Without gathering all the user traffic information and analyzing user trends, which is a violation of privacy ethics, we do analyze connection protocol behaviors and following created unintentional connections towards an Internet address. It doesn’t matter if it is a new site or a cached site, even it isn’t included in any databases, a recently started traffic is analyzed on the fly; without privacy violation, and determined either intentional or unintentional connection. It is a security pro-work. We got it covered. – Attacker Call-Back Traffic Analysis : Determining a traffic started unintentionally and/or without user knowledge even hiding itself in many ways; we can detect it. It doesn’t matter if it is a known hacker traffic, included in any databases, or an unknown zero-day attack, without privacy violation, we are ready to analyze it automated and on the fly. It is a security pro-work. We got it covered.
– Attacker Call-Back Traffic Analysis : Determining a traffic started unintentionally and/or without user knowledge even hiding itself in many ways; we can detect it. It doesn’t matter if it is a known hacker traffic, included in any databases, or an unknown zero-day attack, without privacy violation, we are ready to analyze it automated and on the fly. It is a security pro-work. We got it covered. – Attacker On Initial Phase Prevention : Even all of your prevention techniques and detection techniques fail; we do help for fighting back! An attacker after infiltrating to the network needs to map it; finding valuable server assets or stating the size of a network, we are there to confuse and stop the attack. We can detect mapping intentions and prevent it. Furthermore, we analyze the traffic back to the attacker and stop sequel traffic on the fly. We got it covered.
– Attacker On Initial Phase Prevention : Even all of your prevention techniques and detection techniques fail; we do help for fighting back! An attacker after infiltrating to the network needs to map it; finding valuable server assets or stating the size of a network, we are there to confuse and stop the attack. We can detect mapping intentions and prevent it. Furthermore, we analyze the traffic back to the attacker and stop sequel traffic on the fly. We got it covered.

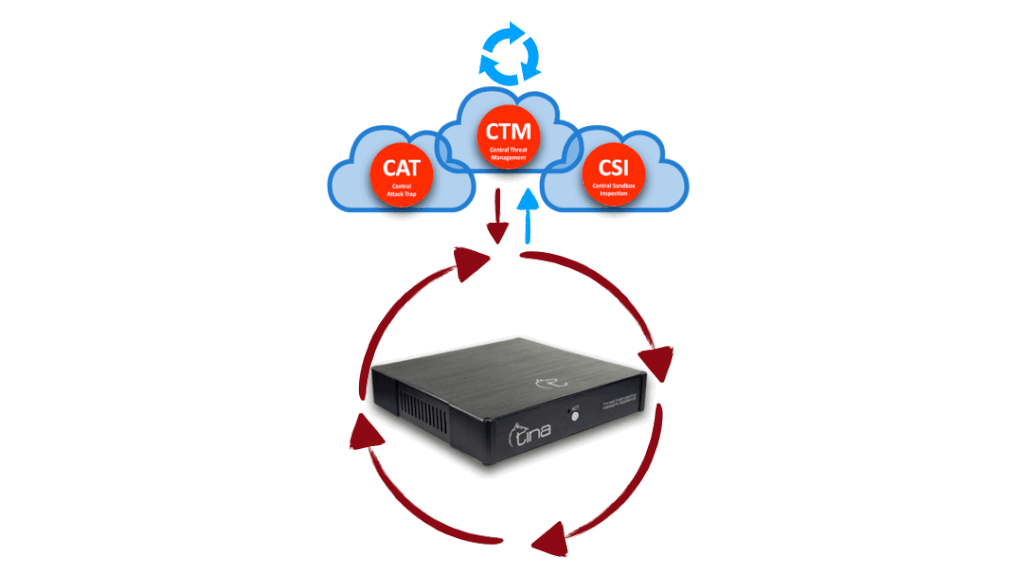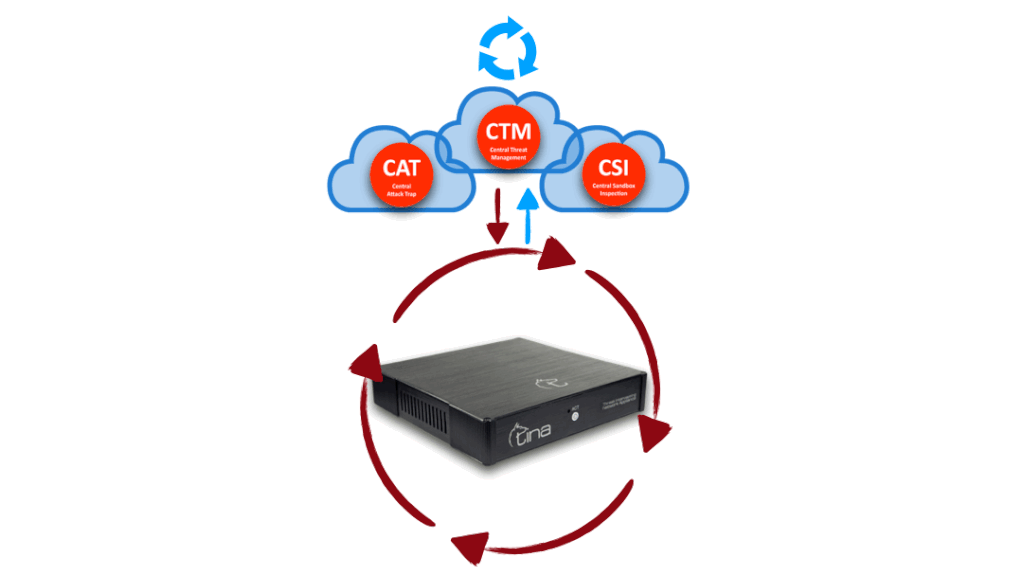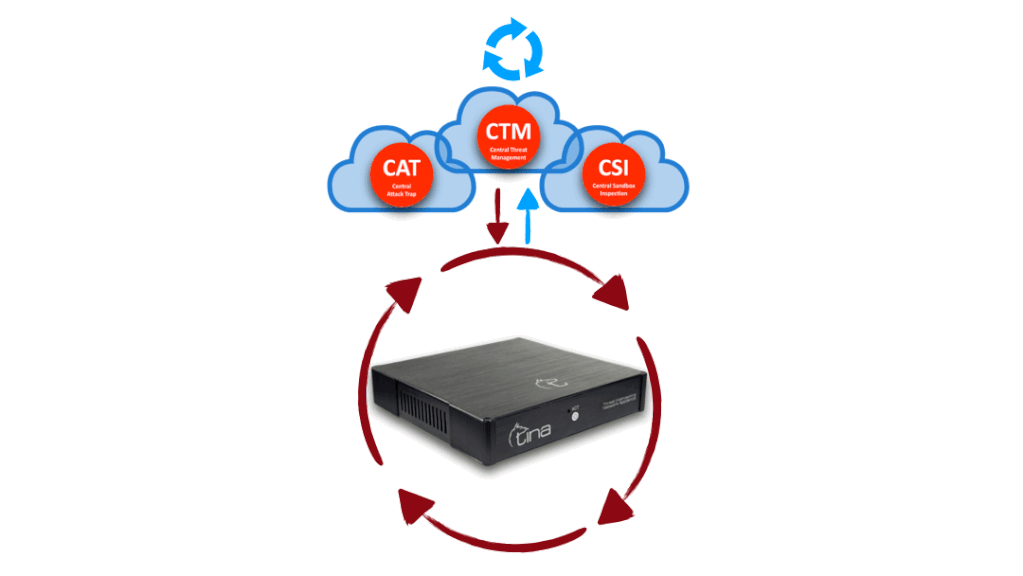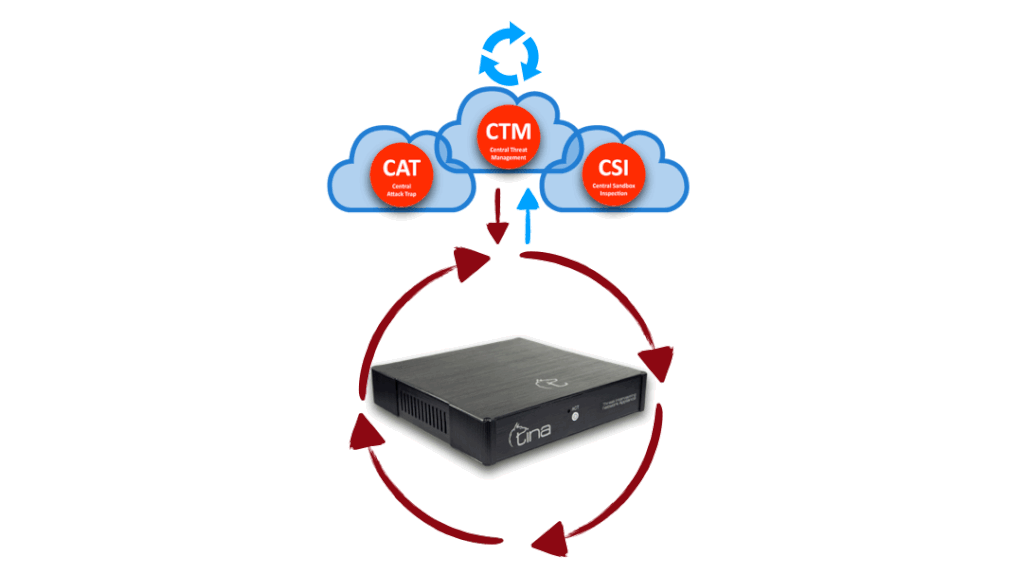
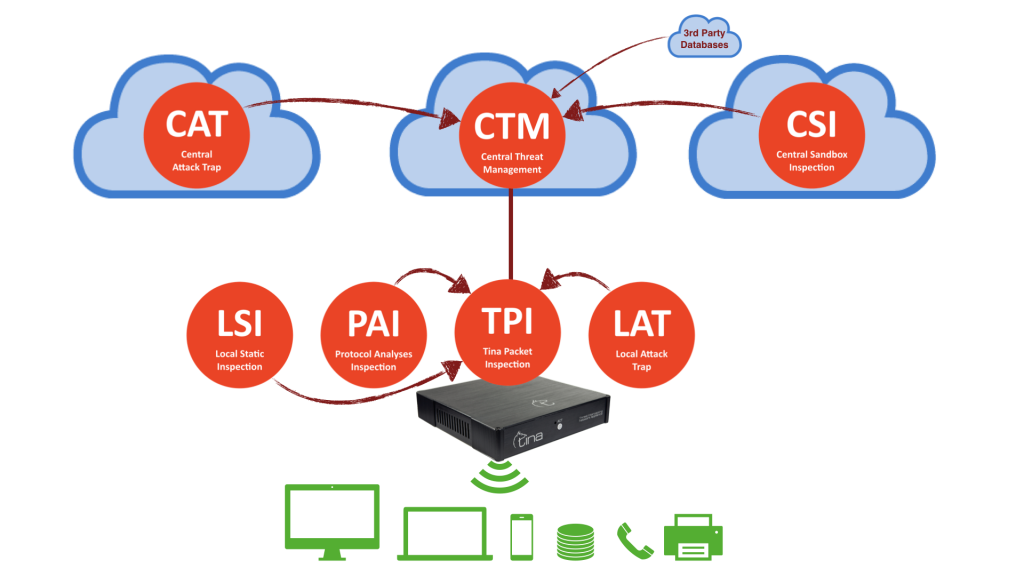











We won’t give you exact numbers, sorry, but let us give a little clue; our CTM has it’s own upscaling capability, by means of traffic, computing, storing and managing itself. It is also designed failsafe for high availability, placed on cloud, on different geographic locations. We know the requirements for being best and we tried harder for it.

We won’t give you exact numbers, sorry, but let us give a little clue; our CAT has it’s own specific sectors settled around the world and 7/24 actively collecting info from various databases even underground (deepweb) systems and managing itself. It is designed for high availability, placed on cloud, on different geographic locations. We know the requirements for being best and we tried harder for it.

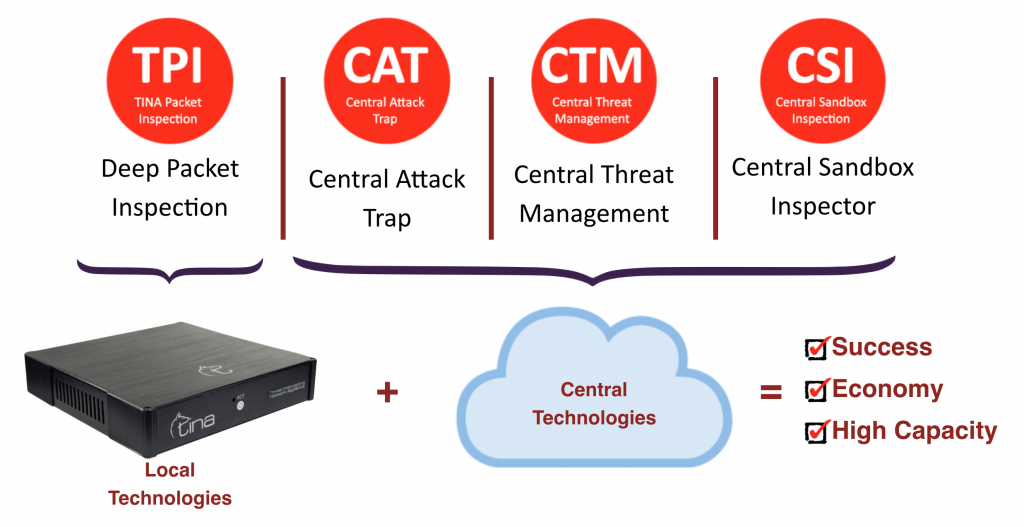
Feeds other Tina systems and technologies with central analysis, including both automated and supervised laboratory analysis.
Multiple Structure
Monitoring and Support System
Data Privacy and Protection
Prevention Techniques Against Anti-Sandbox
We won’t give you exact numbers, sorry, but let us give a little clue; our CAT has it’s own upscaling capacity, by means of traffic, computing, storing and managing itself. Not only analyzes your files, also analyzes roaming objects on Internet around the world, 7/24 actively. It is designed for high availability, placed on cloud, on different geographic locations. We know the requirements for being best and we tried harder for it.


Feeds other TINA systems and technologies with local analysis, including both on the fly and automated follow-up laboratory analysis.
We won’t give you exact numbers, sorry, but let us give a little clue; our TPI has it’s own capacity manager system in it, by means of traffic, we do 1Gbps in 1 seconds. We do not use our hardware capacity more than 50% in full load, by all means; computing, storing and managing. We have hardware bypass and software precautions (we give detailed infos only to TINA owners). We know the requirements for being best and we tried harder for it.

Feeds other TINA systems and technologies with local analysis, including both on the fly and automated follow-up laboratory analysis.
We won’t give you exact numbers, sorry, but let us give a little clue; our LAT has it’s own capacity manager system in it, by means of traffic, we do 1Gbps in 1 seconds. We do not use our hardware capacity more than 50% in full load, by all means; computing, storing and managing. We have hardware bypass and software precautions (we give detailed infos only to TINA owners). We know the requirements for being best and we tried harder for it.

Feeds other TINA systems and technologies with local analysis, including both on the fly and automated follow-up laboratory analysis.
We won’t give you exact numbers, sorry, but let us give a little clue; our PAI has it’s own capacity manager system in it, by means of traffic, we do 1Gbps in 1 seconds. We do not use our hardware capacity more than 50% in full load, by all means; computing, storing and managing. We have hardware bypass and software precautions (we give detailed infos only to TINA owners). We know the requirements for being best and we tried harder for it.

Feeds other TINA systems and technologies with local analysis, including both on the fly and automated follow-up laboratory analysis.
We won’t give you exact numbers, sorry, for users with enormous file amounts, our LSI system have expandable hardware options, also can run multiple LSI units in one location, fully compatible with other TINA systems. We have bypass and software precautions (we give detailed infos only to TINA owners). We know the requirements for being best and we tried harder for it.

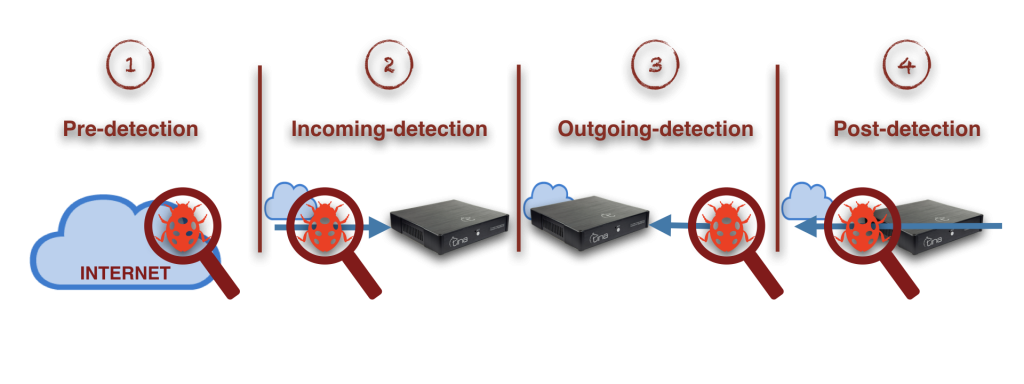
TINA examines internet traffic in bridge mode and does not require any routing. It is used without need for rule based management or an active modification. Management interface does not require learning; does not have any additional training load or active follow-up requirement.
TINA not just uses static analysis, but also is able to provide a stronger behavior analysis and dynamic analysis with honeypot services included.
TINA has two layer file analysis in which stable conclusions are made faster by unique static-file characteristic analysis and dynamic analysis running on a real operating system. TINA sandbox analysis does not only include files, but also includes analysis of links and strong against especially browser based attacks.
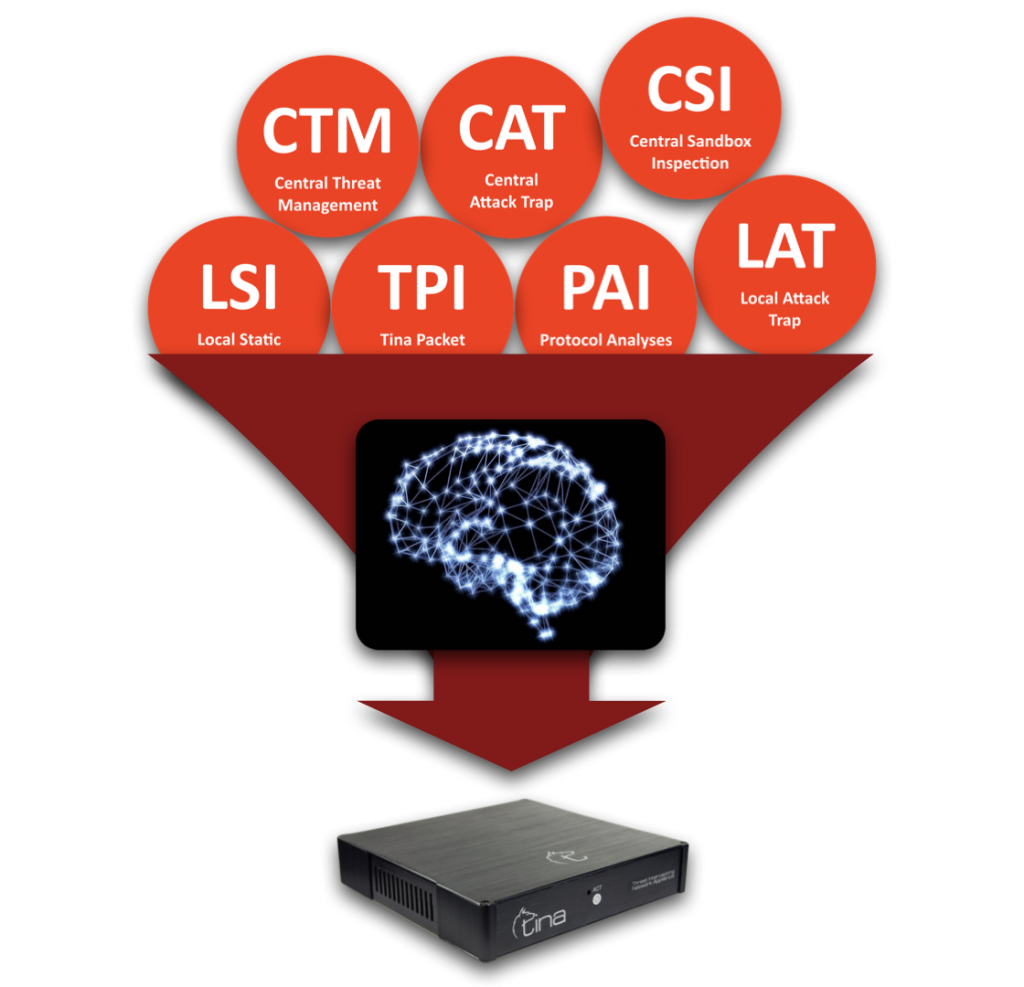
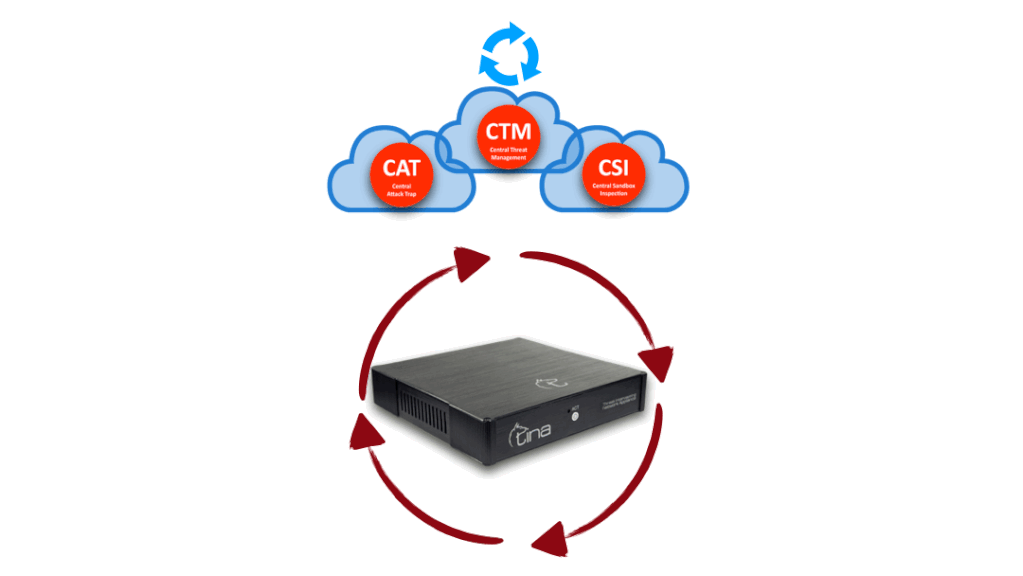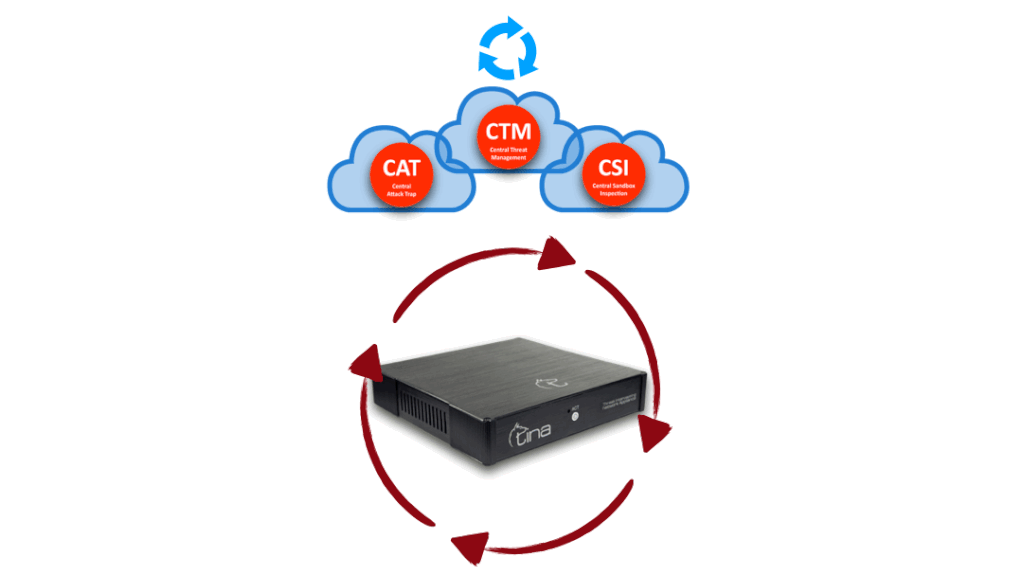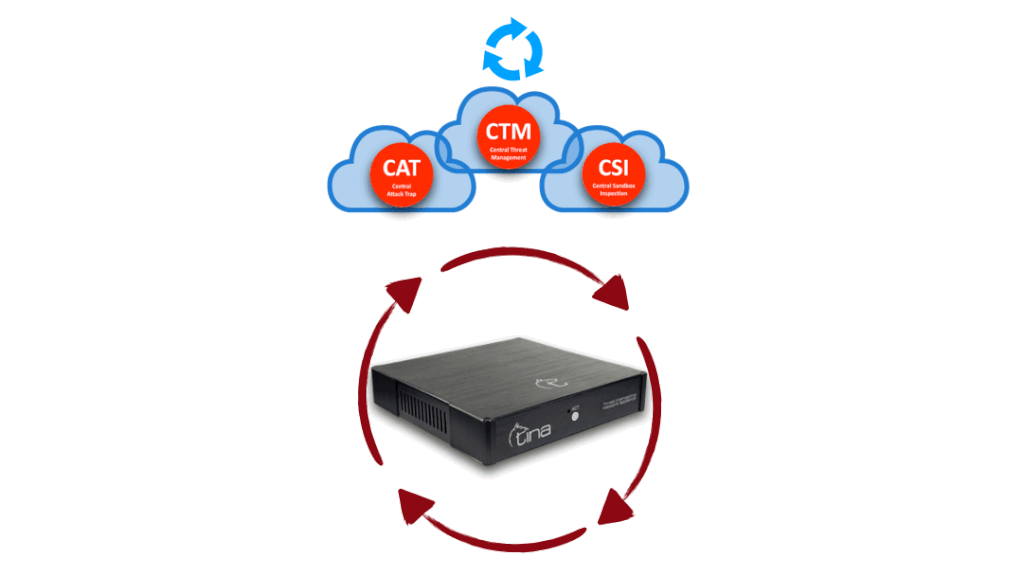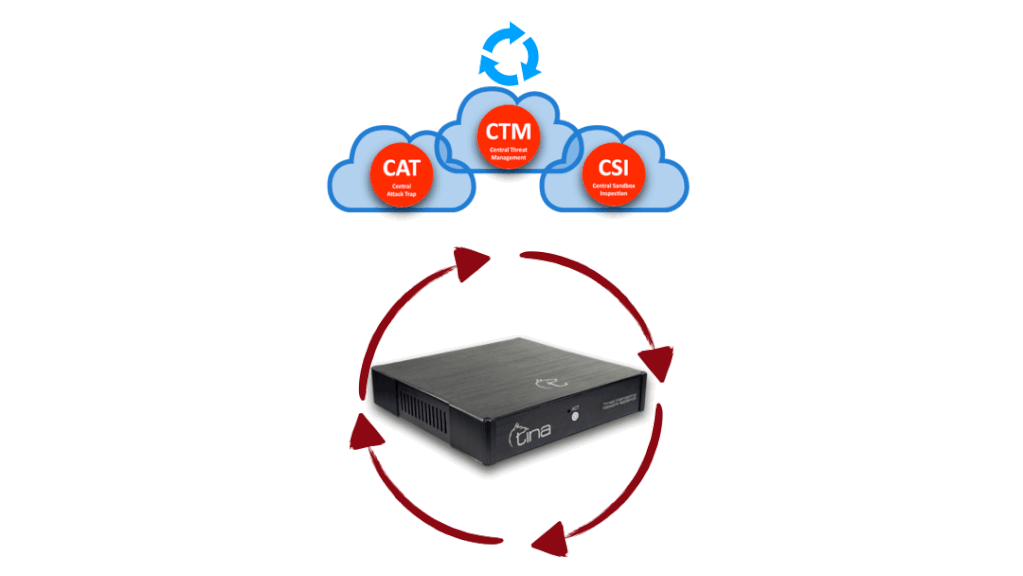
TINA has a unified central data base mechanism like a neural network; that is feed by both local appliances and scattered worldwide intelligence network. Live feeds are shared among along all TINA network to increase success of defence.



